You Want a VPN for Your Phone, Because Apps.
May 16, 2025
7 mins read

VPN: phone, not desktop. WiFi: N/A.
These statements are correct. Or at least as correct as is applicable to the general user in the scope of the following contextual blog which generally recommends that:
“Yes, it’s probably a good idea to be thinking about getting a paid, reputable VPN for your phone.”
You see, when I get bored, I farm a certain class of software bugs for bug bounty money which I then donated to a local charity because:
- It’s easy to prove, requiring no special software.
- The bug is high impact in nature.
- No one else is checking this bug class because they think they actually understand the “Who needs a VPN when you have HTTPs?” argument
So before you dismiss my opinions as more unfounded rhetoric of snake-oil marketing, please consider that I quite literally have reciepts to back it up.
Privacy
The easiest way to enable privacy is to simply not do anything at all, but that’s pretty boring. Your internet service provider can see the servers you’re talking to. If you use a VPN, the VPN provider can see the servers you’re talking to.
In this scope, the main privacy benefit of VPN providers is that they make claims not to log or sell this data, and it’s implied that since you’re paying them they are inclined to uphold these expectations. In the long run, many providers say one thing and do another. Or do the right thing and get sold to another company that then does the wrong thing.
In the end, if you’re selecting a VPN provider pick one that’s been served a legal court order request to disclose their user’s infromation and provided things that meet your expectations.
But I don’t want to talk about privacy.
Security
Privacy and Security go hand-in-hand. Seperating them ins’t really possible, but for the sake of brevity I’m going to pretend you can, ignore a lot of things, and try to get to my point as fast as possible.
Encryption is a security method. It scrambles up the bits and bytes transmitted over the wire which is good for privacy since malicious actors cannot peer inside. Encryption also facilitates methods so that the data cannot be tampered with. Additionally it can support authenticating that the remote server is who it says it is via a trust of an authority.
HTTPS
You don’t need a VPN to use HTTPS, and HTTPS enables encryption so that you get all of the benefits above.
On your computer, your browser (Chrome, Firefox, Edge, Safari, etc…) are actually quite security hardened. When certain privacy, security, or authority expectations aren’t met, you get a big warning that requires several clicks to bypass. This is good and expected.
Similarly, on your phone (Android, iOS, etc…) when using your browser (Chrome, Firefox, Edge, Safari, etc…) you get the same or similar warnings when these expectations aren’t met. This is good and expected.
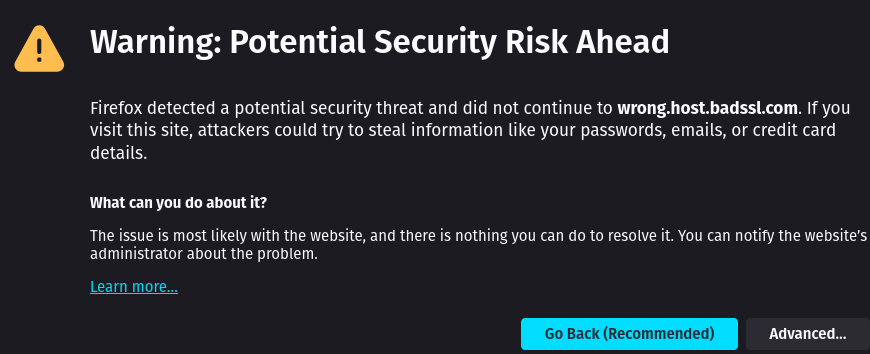
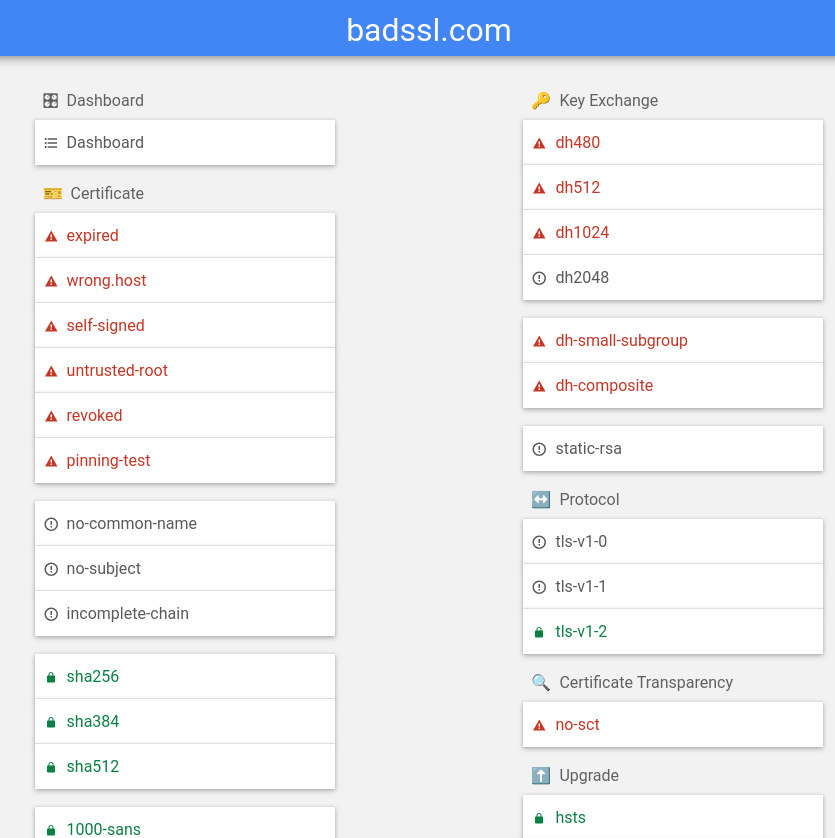
There’s a handy site I like to use called https://badssl.com/ to trigger all of the pass/fail/warn cases for using HTTPS.
Phone’s have Apps
Now that we’ve established that the smartest cryptographic and security minds in the world have actually managed to create something that actually does a really good job, let’s talk about the antithesis of that: App Developers.
You know, those fancy icons on the screen of your phone. Some come with preinstalled apps. You might install some apps for social media, banking, photos, games, lifestyle, etc…
Have you ever clicked a link inside those apps where it didn’t open the browsers we’ve already established are quite secure? App developers don’t want you leaving their apps, they want them “sticky”, so they’ll often create a pseudo-browser inside the app using technologies like a “WebView”. On iOS I’m talking about the window that pops up that looks like this.
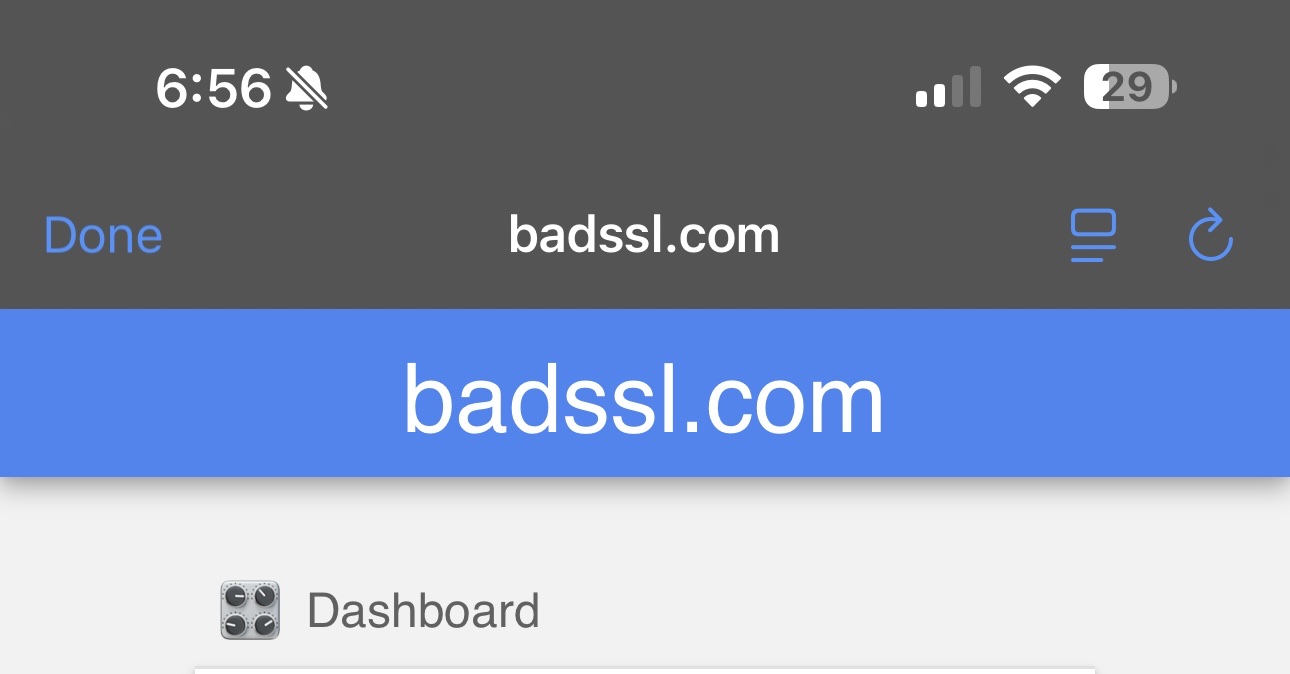
Hopefully this is the part of the blog where it finally clicks that “oh I recognize that and OH MY GOD YOU’RE TELLING ME THAT THING I SEE ALL THE TIME CAN TRANSPARENTLY DISABLE HTTPS VALIDATION???!?!?!?”
And because that psuedo-browser feature was likely written by a developer at a company who isn’t trusted with the private key to their corporate development server for testing, they probably disabled HTTPS validation features on that WebView when they built it.
Did that developer remember to flip that configuration back so that strict HTTPS validation occurs when the app was published and you, the end user, downloaded it?
If not, every link you click in that app no longer has any of the benefits of HTTPS. All of the things that should throw a massive warning from badssl.com, no longer do. This is bad and unexpected.
The harsh reality
It’s quite difficult to accidentily disable HTTPS validation on your computer’s browsers. It’s also quite difficult do that on your phone’s browsers.
But when an app developer makes a mistake, you inherit all of the risk with little more than a tap-to-download of installing the app. You probably have more than a few apps installed on your phone. This risk isn’t siloed to just phones, most computer operating systems support apps of various kinds as well, but the app ecosystem is decidedly stronger on mobile devices.
Do app developers actually make these mistakes?
Yes. Sometimes several times in a row, repeating a cycle of remediation and failure endlessly, for the bug bounty benefits of being donated to my local charity.
I only install massively popular apps with big security budgets, surely this problem is specific to small novice developer shops?
No. No, man. Shit no, man. I believe you get your ass kicked saying something like that man.
Seriously though, it’s mostly those massively popular apps with big security budgets that have bug bounty programs in the first place.
How does a VPN help here?
Well, when the privacy, security, and authorization benefits of encryption via HTTPS are thrown in the trash due to a fairly common developer mistake in apps, you can regain some of those benefits by wrapping the entire connection using a VPN.
In summary, HTTPS is all that most people need on a desktop computer. However, there’s some serious gaps in the mobile phone ecosystem unique to apps and app developers that cannot be easily remediated at scale, and the surface area of the risk is massive to cover.
For those reasons, as a general user, I recommend using a VPN for your phone.
Not because the general user is at any risk from WiFi Machine-In-The-Middle hijacking attacks, but because the general user is at a fairly high risk of an app developer compromising their security and privacy to the extent that they are operating at a comparable level of security as could be expected in 1994, the year HTTPS was introduced.
I think that’s a fairly reasonable to advocate for.
Don’t believe me? Well, start opening apps and find places where you can paste a link for https://badssl.com and open the app’s psuedo-browser. And then set a reminder to do that once a month when the app releases a new update. I’ve already found plenty, but I only check apps that I use regularly. You’ll find the unknown threat of your own with a little patience.
Sharing is caring!